FIDO2 vs Evilginx
Introduction
This blog is about keeping Microsoft 365 user accounts safer from phishing attacks, specifically from those sneaky reverse proxy moves that bad actors use to get around multi-factor authentication (MFA). We’re going to tackle this by setting up FIDO2.
First off, we’ll walk through the reverse proxy phishing lab environment which uses Evilginx. It’s a tool that’s known to cause trouble for MFA. Then, we’ll show you how these attacks happen in a straightforward way. After that, it’s all about FIDO2 – setting it up to help protect your user accounts from these types of attacks.
Ready for a no-nonsense guide to keeping your accounts secure? Let’s dive in.
Reverse proxy phishing lab – Evilginx
Evilginx utilises phishlets and lures to mimic authentic login pages and entice unsuspecting users. In our environment, we’ve crafted a specific lure targeting Microsoft 365. When a user, such as Alex, interacts with the phishing link, they encounter a proxied login page.
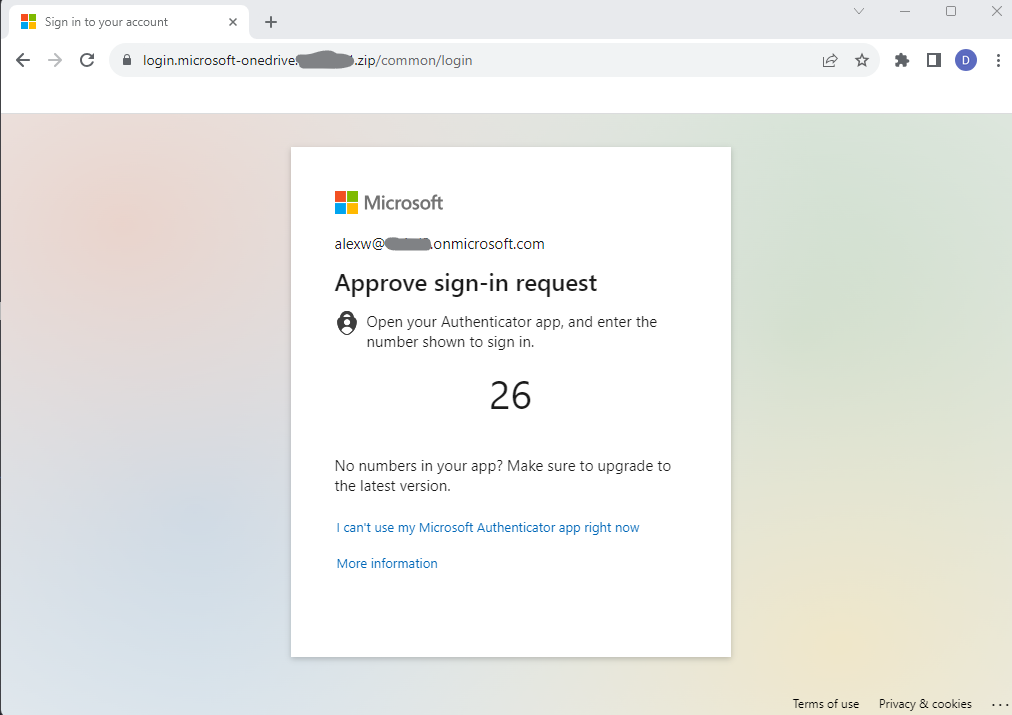
Caption 1: reverse proxy login page capturing MFA
This page is designed to steal credentials including MFA session cookies, illustrating the potential impact of a phishing attack with the captured session information shown below.
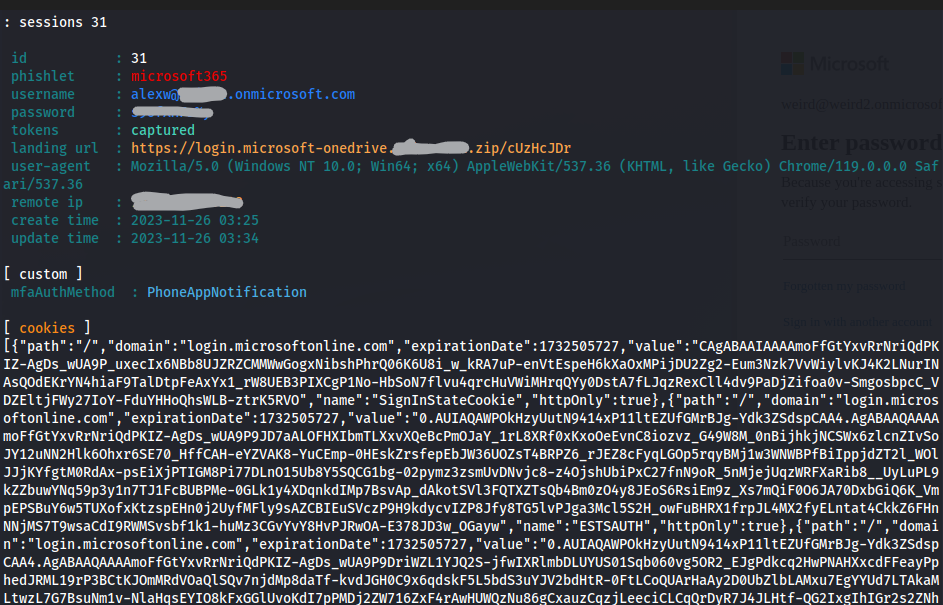
Caption 2: Evilginx captures login information including MFA session cookies.
After importing these cookies into a web browser on our Kali Linux attack box, we are able to log in as Alex and have full access to his email, Teams and OneDrive.
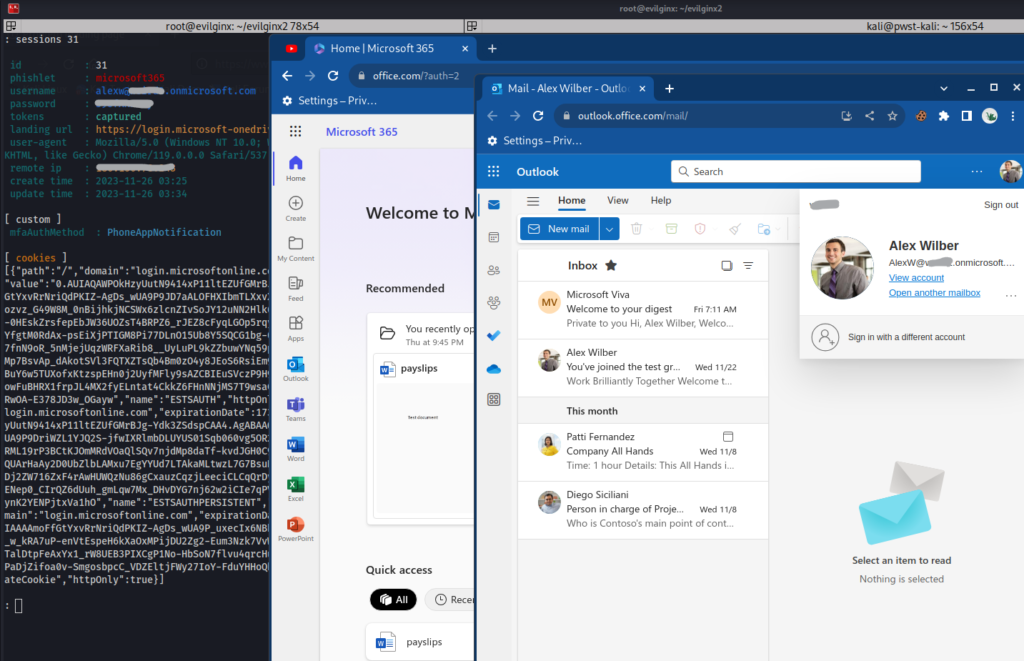
Caption 3: Attacker logged in with captured credentials.
We now look at switching to FIDO2 to help protect your user accounts from these types of attacks.
Using FIDO2
FIDO2, or Fast Identity Online 2.0, represents an advanced authentication framework designed to enhance online security. It introduces a passwordless authentication approach, relying on public-key cryptography to authenticate users. FIDO2 aims to mitigate vulnerabilities associated with traditional password-based systems, providing a more secure and user-friendly authentication experience. This innovative framework has gained widespread adoption and support, offering a promising alternative to traditional authentication methods.
To set up in the lab environment, we first navigate to the Azure portal to enable both FIDO2 security key and Temporary Access Pass under Security | Authentication Methods | Policies. Temporary Access Pass is required for the initial onboarding. Please note the following section borrows extensively from Jan Bakker’s excellent blog post: Use a FIDO2 security key as Azure MFA verification method – JanBakker.tech
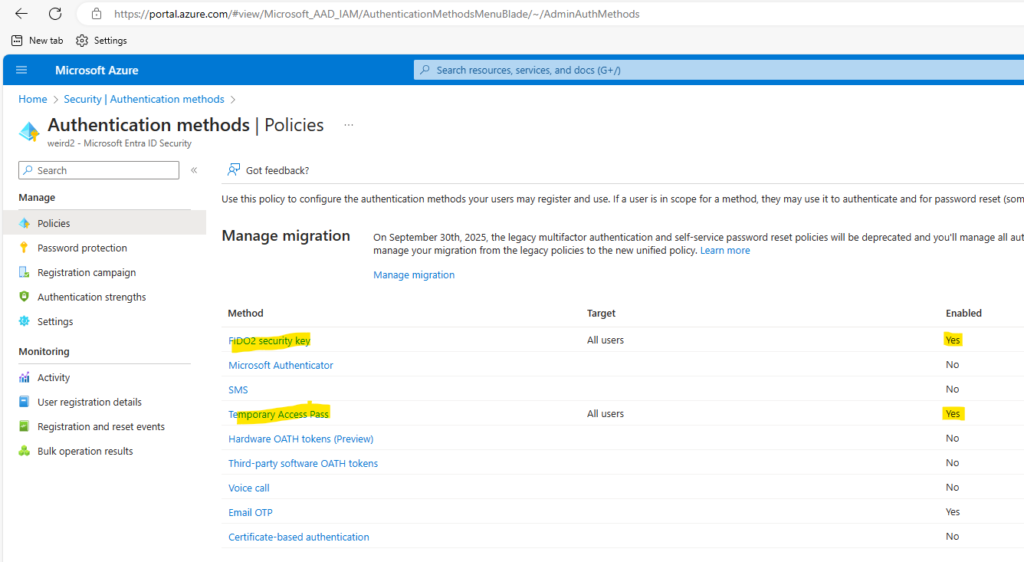
Caption 4: enable both FIDO2 security key and Temporary Access Pass Authentication Methods
Then add Temporary Access Pass authentication method to the user.
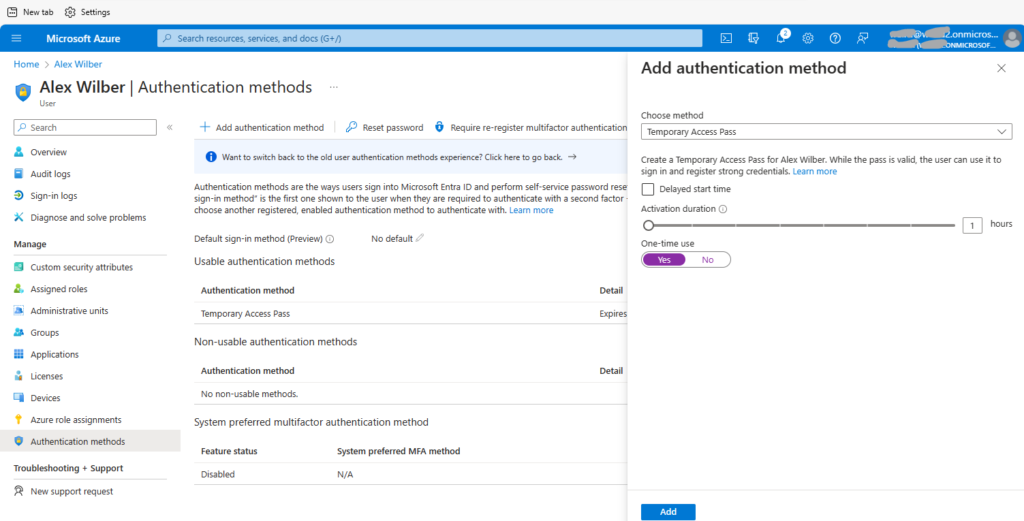
Caption 5: Add Temporary Access Pass authentication method to the user
Provide the Temporary Access Pass details to the user to set up their security key. For more details follow: Set up a security key as your verification method – Microsoft Support
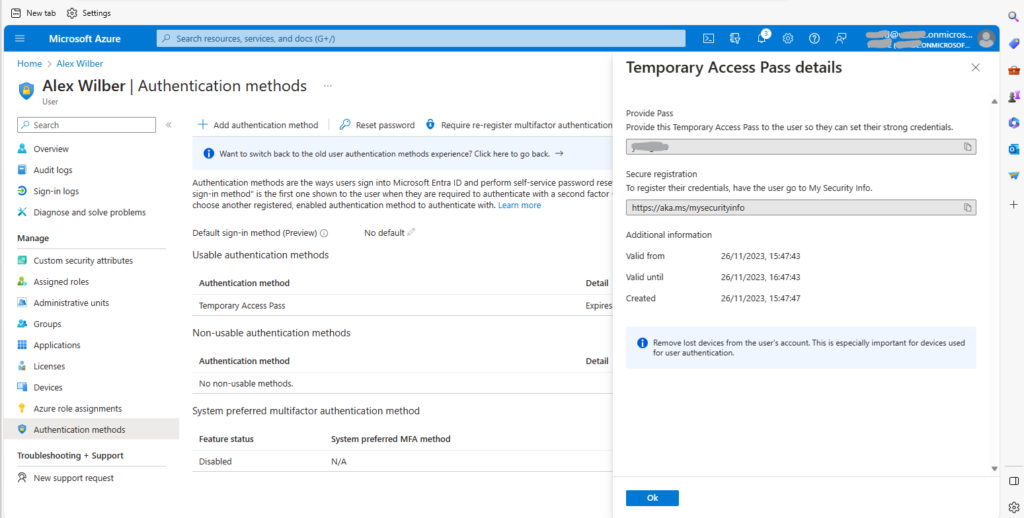
Caption 6: Temporary Access Pass details
Ensure that Multifactor Authentication is required using Conditional Access policies.
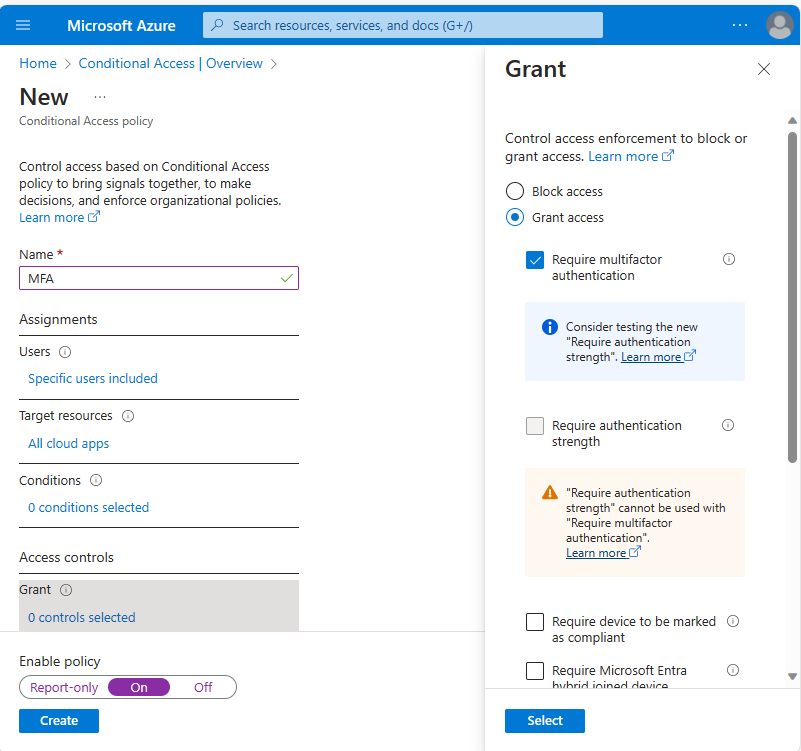
Caption 7: Require multifactor authentication in Conditional Access policies.
Once we have this all configured, it is now time to test FIDO2 vs Evilginx ! And I’ve been Rickrolled by Evilginx … my testing machine IP address was blacklisted … this is actually a thing!
Caption 8: RickRolled by Evilginx
I removed my IP address from blacklist.txt and continue to test with FIDO2 enabled using the previous lure. Success!!! Implementing FIDO2 was effective at preventing Evilginx from being able to bypass MFA!
Conclusion
Implementing FIDO2 emerged as an effective defense, thwarting Evilginx from bypassing MFA. This test affirms the efficacy of FIDO2 in countering reverse proxy phishing attacks, underscoring its significance in fortifying user accounts against evolving threats.
Resources and References
- GitHub – kgretzky/evilginx2: Standalone man-in-the-middle attack framework used for phishing login credentials along with session cookies, allowing for the bypass of 2-factor authentication
- Use a FIDO2 security key as Azure MFA verification method – JanBakker.tech
- Set up a security key as your verification method – Microsoft Support
- I Stole a Microsoft 365 Account. Here’s How. – YouTube
