AI-Driven JavaScript Obfuscation of a HTML redirector
Introduction
This article details utilizing an AI model, specifically OpenAI’s ChatGPT, to create a Python script to generate an HTML document capable of redirecting to a specified URL with a designated title, incorporating simple but effective JavaScript obfuscation.

What is a HTML redirector?
In this post, we refer to a HTML redirector as a piece of code embedded in an HTML file that automatically sends users to a different URL. In malicious contexts, bad actors obfuscate these redirectors within HTML attachments to:
- Conceal Malicious Intent: By hiding the true nature of the redirector, attackers can trick users into visiting harmful sites, often used for phishing or malware distribution.
- Bypass Security Filters: Obfuscation helps in evading detection by security software, which might otherwise recognize and block a straightforward redirector.
Such tactics are particularly prevalent in email-based attacks, where an unsuspecting user might open an HTML attachment thinking it’s harmless, only to be redirected to a malicious site.
The Inception of the Script
In response to a query, ChatGPT developed a Python script that employs multiple encoding techniques. This script is designed to obfuscate JavaScript embedded within an HTML document, showcasing AI’s capability in solving programming tasks. Through the use of hexadecimal and Base64 encoding, the script transforms clear text URLs and titles into obfuscated strings, demonstrating a practical application of AI in the field of data security and web development.
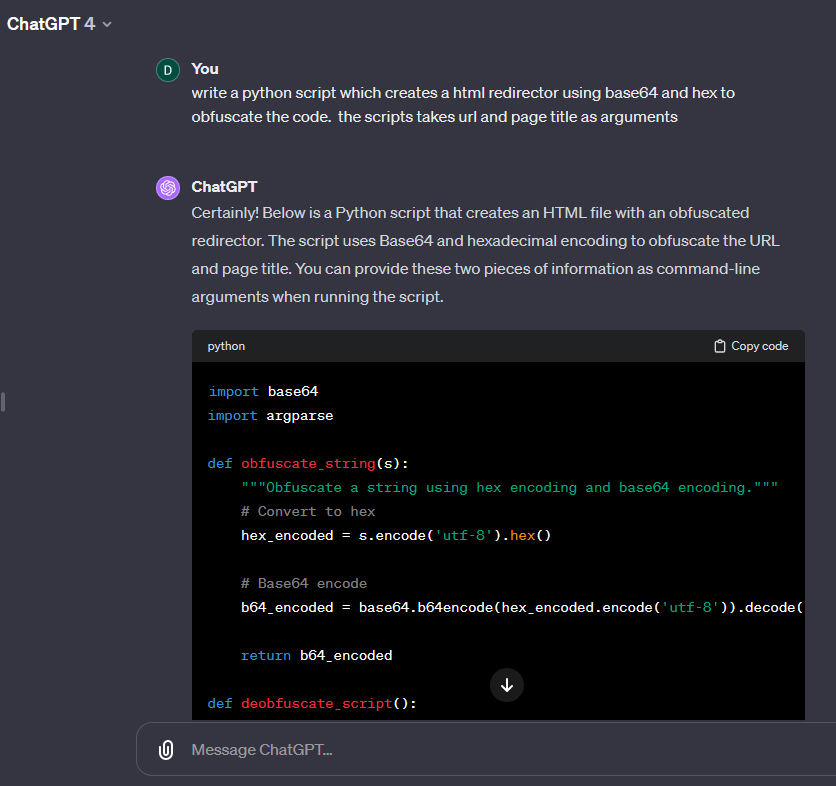
Script Overview
The primary function of this script is to disguise a URL and a page title using encoding methods, subsequently generating an HTML file that, when opened, redirects the user to the encoded URL and displays the encoded title. This script serves as an example of how data can be concealed and then revealed, showcasing the principles of obfuscation in web development.
The script operates in several stages:
- Encoding Process: Initially, the script takes the given URL and title and encodes them using a combination of hexadecimal and Base64 encoding. This process transforms the plain text into an encoded string that appears unrelated to the original content.
- HTML File Generation: The script then generates an HTML file containing a JavaScript function responsible for decoding the obfuscated data. This HTML file, when executed in a browser, activates the JavaScript, which decodes the URL and title back to their original forms.
- User Interaction: The final output is an HTML file that, to the end-user, functions as a typical webpage redirecting to a specified URL with a given title. The intricacy of the script lies in its ability to hide these details until the very moment the HTML file is opened.
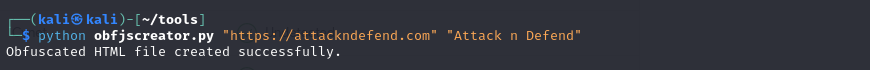
Technical Analysis of the Obfuscation Technique
This section offers an examination of the obfuscation technique utilized by the script. It serves as a practical example of obfuscation, demonstrating data encoding and decoding.
- Encoding Methodology: The script employs a dual-phase encoding strategy. Initially, it converts the URL and title into a hexadecimal format, assigning each character its corresponding hexadecimal value. Subsequently, it encodes this hexadecimal string using Base64 encoding, a technique that converts binary data into an ASCII string format.
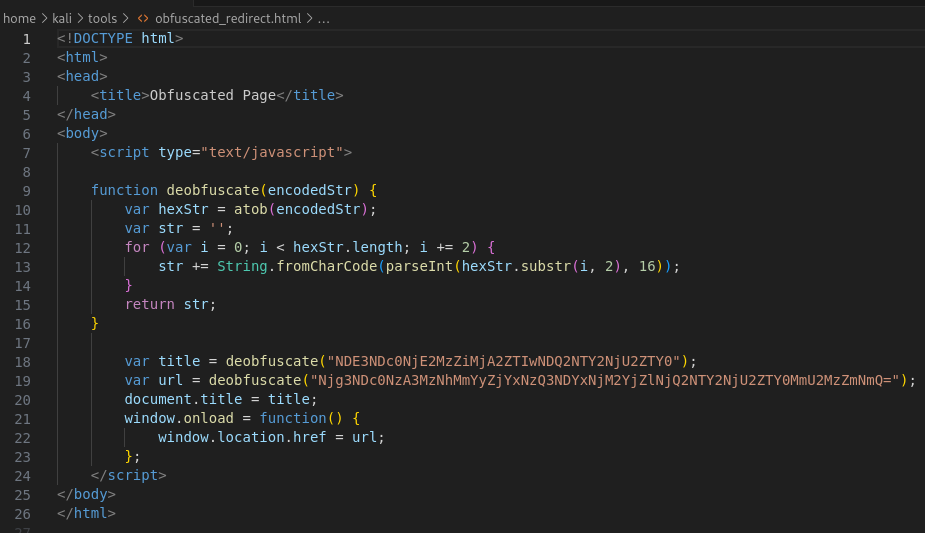
- JavaScript Decoding Functionality: Integral to the generated HTML file is a JavaScript function crafted to invert the encoding process. This function decodes the Base64 string back to hexadecimal format and then translates the hexadecimal values into their original characters, crucial for uncovering the concealed URL and title.
- Browser Execution Process: Upon opening the HTML file in a browser, the embedded JavaScript function activates, decoding the obfuscated strings and revealing the actual URL and title. Consequently, the browser proceeds to redirect to the decoded URL, displaying the decoded title in the tab.
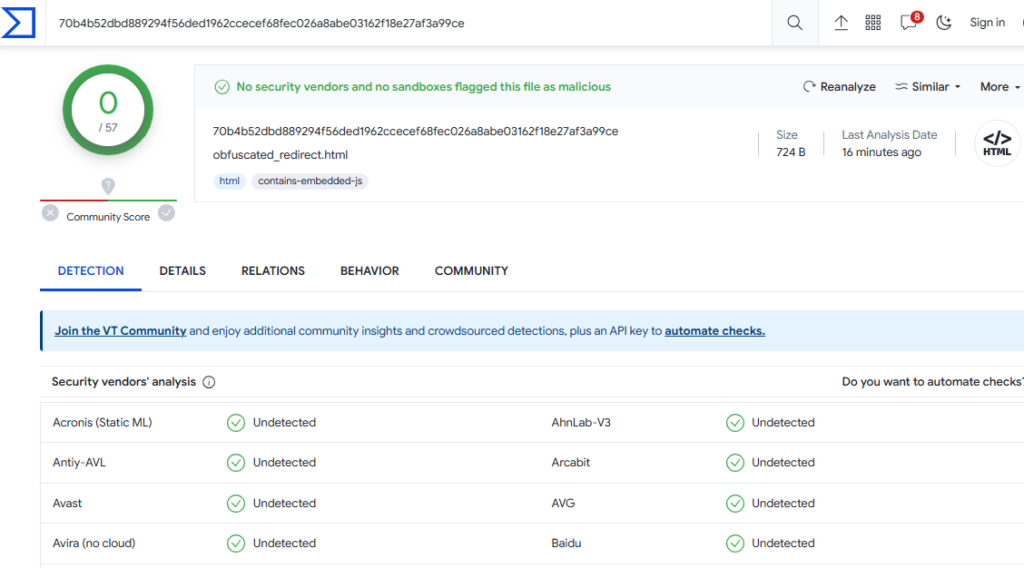
KleenScan and VirusTotal Analysis
The JavaScript embedded in the HTML file systematically decodes the obfuscated strings from Base64 and then converts them from hexadecimal back to their original string form, effectively retrieving the original URL and title.
The image below shows the KleenScan analysis of the created HTML file, which has been evaluated against 40 different antivirus engines, with the results not being distributed. In this particular analysis, none of the antivirus engines flagged the file as potentially malicious.

The choice not to distribute results is significant, especially in the context of cybersecurity and malware analysis. Malware authors, for instance, might prefer not to distribute the results of such scans for several reasons:
- Avoiding Detection: By not distributing the results, malware authors can test their code against numerous antivirus engines without alerting the security community. If these results were shared, antivirus companies could update their signatures and detection algorithms, leading to quicker identification and neutralization of the malware.
- Stealth Tactics: Keeping the results private assists in maintaining the stealthiness of the malware. If results are distributed, it increases the chances of detection and analysis by security researchers, leading to faster countermeasures.
- Continuous Development: Malware authors often use these types of scans to refine and evolve their malicious software. By understanding which antivirus engines can and cannot detect their malware, they can iteratively improve their techniques to bypass security measures more effectively.
Similarly, when the same HTML file was analyzed using VirusTotal, a widely recognized online service that aggregates numerous antivirus products and online scan engines, the results were consistent with KleenScan.
Implications and Applications
The practice of code obfuscation, though technically intriguing, can be utilized for malicious purposes. These include evading security monitoring systems and complicating the process of malware analysis, thereby posing significant security risks.
Given these potential misuses, it is crucial that such techniques are employed with ethical discernment. The most appropriate applications of code obfuscation are within the realms of cybersecurity defenses or educational environments, where they can contribute to the development of more robust security measures or enhance learning experiences. In these contexts, obfuscated scripts can play a role in simulating security threats in a controlled manner, aiding in the training of cybersecurity professionals, or testing the effectiveness of security solutions.
Conclusion
While the script primarily focuses on straightforward yet effective encoding methods, the incorporation of more sophisticated or additional techniques, such as intricate string manipulation, could potentially augment both its complexity and efficacy. This endeavor, a collaborative synthesis of human inquiry and artificial intelligence, exemplifies the vast potential of AI in fostering inventive solutions within the programming sphere and highlights the critical role of understanding and responsibly applying obfuscation techniques in today’s digital era.
